It was just a quick invoice check from a café’s Wi-Fi — until a client’s financial report leaked into the wrong hands.
Today’s digital entrepreneurs move fast: remote teams, cloud accounts, instant payments. But with that speed comes exposure. Financial data breaches, platform restrictions, and digital surveillance are now part of the global business game.
This guide uncovers the five biggest digital risks you’ll face as a financial entrepreneur in 2025 — and the smart tools, like encryption and a VPN app, that can keep your operations secure.
Risk #1: Public Wi-Fi and Unencrypted Connections

From hotel lounges to co-working spaces, public Wi-Fi is a convenience with hidden costs.
If you’ve ever reviewed invoices at a café, uploaded a contract at the airport, or checked your balance from a hotel lobby — you’ve taken a digital gamble. These networks, though convenient, are often unsecured, meaning anyone on the same connection could potentially “listen in” on what you’re doing.
This isn’t a scare tactic — it’s how man-in-the-middle attacks happen. Picture it like this: you’re handing a sealed envelope to a courier (your data to the internet), but someone quietly swaps it out before it reaches its destination. That “courier” could be a rogue device on the same Wi-Fi, intercepting your credentials, session tokens, or even entire documents.
🔍 Common risks include:
- Auto-login cookies being stolen (giving hackers direct account access)
- Banking passwords captured in real time
- Invoice data exposed during upload
💡 What to do:
✅ Avoid using public Wi-Fi for accessing banking, accounting software, or sensitive dashboards unless you have no other option.
✅ Use encryption tools, like secure messaging apps (Signal, ProtonMail), and always make sure the website you’re visiting starts with https:// — the “s” means encrypted.
✅ Use a virtual private network (VPN) on all public networks. A VPN app encrypts the entire connection from your device to the internet. Think of it like a private tunnel through a crowded highway. Solutions like X-VPN are lightweight, fast, and easy to toggle on whenever you’re outside a trusted environment.
Even if you’re just checking transaction logs, a VPN ensures no one else in the café or airport is watching over your shoulder — digitally speaking.
If you’re managing your business from your phone — whether reviewing invoices or sending transfers — using a VPN app for Android adds an essential layer of protection on the go.
Risk #2: Unauthorized Remote Access to Financial Tools
In 2025, remote work is no longer a trend — it’s standard. Most digital entrepreneurs now collaborate with virtual teams, distributed finance staff, and even freelance bookkeepers working across multiple time zones.And as networking goes digital too, professionals increasingly adopt tools like NFC business cards that make secure, contactless connections easier during global travel or client meetings.
This flexibility is great for growth — but without guardrails, it’s also a security trap.
Here’s the problem:
Every login is a potential weak point. If someone on your team logs into QuickBooks from a shared computer, forgets to log out, or uses a weak password, your business data is at risk. Even worse, if your email — the recovery method for nearly every platform — gets compromised, hackers could reset access to your financial tools without ever touching the original accounts.
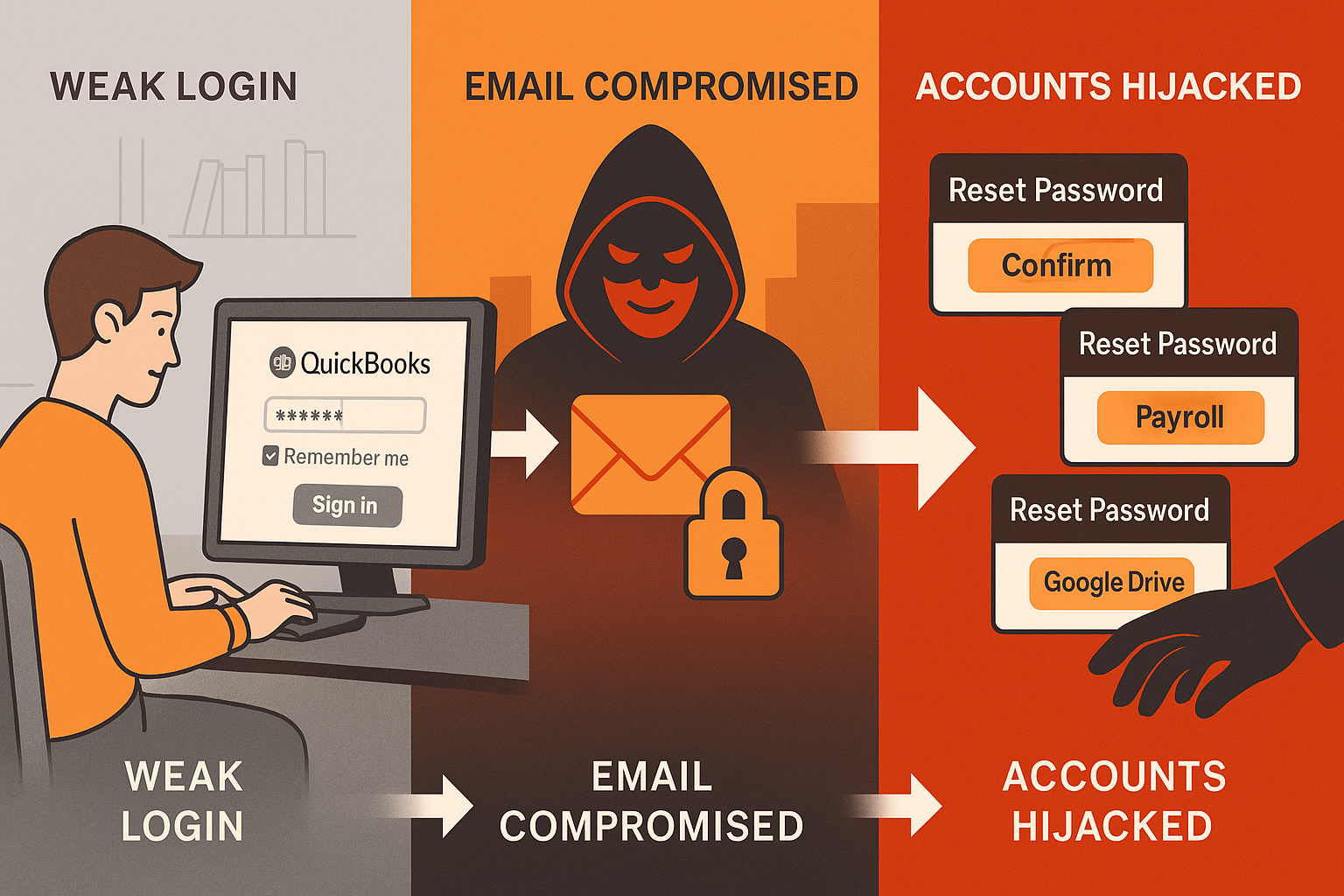
And it doesn’t take a black-hat hacker to do damage. Insecure Wi-Fi, a misplaced laptop, or reused login credentials can all lead to unauthorized access.
🔍 Common real-world mistakes:
- A VA logs into your accounting dashboard from an internet café without protection
- An ex-employee still has access to Stripe or PayPal because revoking wasn’t centralized
- Your own laptop is stolen, and your browser is auto-filled with saved passwords
💡 What to do:
✅ Enforce Multi-Factor Authentication (MFA)
MFA adds a second layer of protection beyond your password — like a one-time code sent to your phone or an app like Authy. Even if someone guesses your login, they’ll still be locked out without that second factor.
✅ Centralize your access control policies
Use admin tools like Google Workspace, Microsoft 365 Admin, or Notion Enterprise to manage which team members have access to which tools — and revoke access instantly when roles change.
✅ Mandate VPN use for remote teams
Not just for you — make it company policy that every remote login must be made through a trusted VPN. This prevents unauthorized geographic access, masks IP addresses, and secures logins from being intercepted.
🔐 Example:
A team member working from Vietnam logs into your U.S.-based tax software. Without a VPN, their location may trigger a block or suspicious login alert. With a VPN, you can route that connection through a U.S. server, keeping everything smooth, secure, and under your control.
Risk #3: Financial Platform Account Hijacking
Fintech platforms have become the financial backbone for modern entrepreneurs. Stripe for payments. QuickBooks for accounting. Wise for international transfers. Revolut for business cards. The convenience is unmatched — but so is the risk.
Every new platform you use creates a new door to your financial operations. And if that door isn’t locked tight, someone else can walk right in.
Cybercriminals don’t need to “hack” your business in the Hollywood sense. They often get in through the digital equivalent of an unlocked door:
- Reused passwords across multiple platforms
- A team member accidentally clicking a phishing link
- An API key shared over email without encryption
- Forgotten logins left active after a team member leaves
In 2024, IBM reported that account-level breaches in small businesses have doubled, largely due to the explosion of SaaS platforms and weak credential hygiene.
This isn’t just about stealing money — it’s about full control. If someone hijacks your Stripe account, they can divert payouts. If they get into your QuickBooks, they can alter tax data. And if your crypto wallet app is compromised, funds could disappear in minutes.
💡 What to do:
✅ Rotate credentials regularly
Change your passwords on financial tools at least every 90 days — and never reuse the same one across platforms. Use a password manager to make this painless.
✅ Use hardware security keys
For platforms that support it (e.g., Google, Coinbase, Amazon), enable physical 2FA devices like YubiKey. It adds an unhackable layer — attackers can’t log in without the physical device in hand.
✅ Monitor location and device login activity
Check platform audit logs to see who’s logging in, from where, and on what devices. Suspicious activity (like an unknown country or new device) should trigger immediate action.
✅ Use a VPN to normalize and secure traffic
VPNs help remote teams route their logins through a consistent IP region, which not only masks physical locations but also prevents false positives or lockdowns from unusual logins.
Risk #4: Surveillance and Regulatory Scrutiny
In certain regions, financial activity — especially involving cryptocurrency, offshore holdings, or politically sensitive clients — may draw surveillance from ISPs or local regulators. Even basic business transactions may be flagged or logged for “compliance” purposes.
This is particularly risky for entrepreneurs operating across borders or in high-censorship markets like China, UAE, or parts of Eastern Europe.
💡 What to do:
- Use VPNs to maintain privacy when accessing financial tools in regulated regions.
- Avoid sending unencrypted financial documents via email.
- Familiarize yourself with data residency laws in your clients’ and team members’ jurisdictions.
Risk #5: Geo-Restricted Access to Critical Services
It’s an overlooked but painful problem: You try to log into a payment processor or tax tool abroad, only to be locked out due to geo-restrictions. Some platforms auto-block access based on IP location or may offer a stripped-down feature set outside your home country.
For digital entrepreneurs working globally, this can delay transactions, payroll, or legal filings.
💡 What to do:
- Before traveling, test critical services using a VPN with multiple server locations.
- Work with platforms that offer regional redundancy or roaming support.
- Keep local backups of essential financial data in case online tools fail temporarily.
Tools Every Financial Entrepreneur Needs in 2025
To thrive in 2025, digital entrepreneurs must think like cybersecurity leaders. Here’s your modern toolkit for protecting sensitive financial operations:
| Tool Type | Example Tools | Why It Matters |
| VPN | X-VPN | Encrypts your traffic, hides location, prevents leaks |
| Password Manager | 1Password, Bitwarden | Secures and rotates complex credentials |
| MFA Authentication | Google Authenticator, Authy | Adds a layer of defense beyond passwords |
| Secure Cloud Storage | Tresorit, Proton Drive | Keeps sensitive documents encrypted |
| Phishing Detection | IRONSCALES, Avanan | Protects against fake invoices and credential theft |
Final Thoughts: Security as a Competitive Edge
Digital risk is no longer just an IT department’s problem — it’s a business model issue. For entrepreneurs handling money, client data, and global access, ignoring cybersecurity is a fast way to lose trust, revenue, or worse.
But the good news? Protecting your digital operations isn’t complicated. It starts with awareness — and with tools like VPNs, smart authentication, and encrypted platforms, you can turn security into your competitive advantage.
After all, in 2025, the safest business is the smartest one.
Frequently Asked Questions (FAQ)
1. Why should financial entrepreneurs care about VPNs?
Because financial data is one of the most targeted assets online. As a digital entrepreneur, you’re handling sensitive client records, payment credentials, and tax documents. A VPN encrypts your internet traffic, making it nearly impossible for hackers — or even your ISP — to snoop on your financial operations.
- Does using a VPN slow down access to financial platforms?
Not if you choose the right one. Modern VPNs like X-VPN use high-speed global servers that minimize latency. In fact, a VPN can improve platform stability if you’re traveling or working in a region with restricted access.
3. Is it legal to use VPNs for business operations?
In most countries — including the U.S., U.K., and EU — using a VPN for business is 100% legal. However, you should never use a VPN to engage in fraud or violate terms of service. VPNs are a legitimate cybersecurity tool used by companies worldwide to protect sensitive data.
4. How do I know if my accounts have been compromised?
Look for red flags: unfamiliar login locations, password reset emails you didn’t request, or locked accounts. Many platforms now offer login activity reports — check them regularly. Better yet, prevent issues by using MFA, rotating passwords, and securing all logins with a VPN.
5. What’s the difference between a VPN and other security tools?
Think of a VPN as a shield for your connection — it protects everything you do online, regardless of the app or website. Tools like antivirus software or firewalls only protect your device locally. Password managers protect credentials, but not your internet traffic. A good security setup uses all of these together.

